Evolution of Ransomware Attacks: An African Focus

Disclaimer: These are just random thoughts in my head which I wanted to share from a personal point of view. Do enjoy.
Out there in the wild, we have seen APT28 exploiting vulnerable Cisco routers and installing backdoors for further attacks.
Right here in Africa, Ransomware groups have changed their modus operandi in the recent attacks that we are seeing lately. They have moved from encrypting files with demand via crypto currencies to now exfiltrating data in large amounts, sending a warning of when they will be released to the public via the DeepWeb.
This of course is beneficial to them knowing Data has become very expensive and companies have backup so it’s pretty much useless when the organisation is just going to format the computers and restore backup.
There is a need to “frustrate, distract, isolate, disrupt and ultimately slow down threat actors capacity to cause pain to organizations”
High Level Africa Security Landscape 2023
A number of ransomware groups such as Lockbit, REvil, MEDUSA and ALPHV/BlackCAT have recently shown that companies in East Africa will become their latest target. Due to the number of vulnerabilities available, most of their attacks are almost automated to identify low hanging fruits.
A few weeks ago(today is 25th April,2023), some of the companies were compromised and their data was exposed. Data worth 500GB and above exfiltrated and leaked. Whilst some kept quiet on the matter, others allegedly paid the ransom for their details to be removed. The latest victim however took a different turn which is a kind of act in Africa which by publicly acknowledging that they have been compromised and even reported to the Office of the Data protection Commission (we have never seen this before and I commend them greatly on their communication strategy).
This is just the beginning as Cyber criminals are about to explore more in the East African space with possibility of later expanding to the entire Africa region. Organizations need to start having Cyber Resilience conversations in the boardroom with level readiness.
The Attack methodology
As a researcher, a simple search query using google dorking or launch of the powerful search engine shodan.io and putting in the right queries reveals a number of systems vulnerable to simple attacks.
A typical example is SMB shares that are still accessible belonging to ERP systems exposing shared drives without a password to authenticate. This takes less than 10 seconds to compromise with simple tools like smbclient
Another is Microsoft Exchange servers with no latest update or has been misconfigured with multitudes of vulnerabilities allowing for an adversary to take over in a very short time.
A very common is eternalblue vulnerability (easy to exploit) still showing on many servers and it gets shocking to see organizations still run old versions of OS in their infrastructure (No they are not honeypots)
To take over the above systems can be automated to target an entire country IP range and filter the easiest to exploit. Hackers do not like difficult networks or systems to compromise when it comes to ransomware attacks.
The Way Forward
We must go back to basics and start moving from Cyber Security (2,3,4) to Cyber Resilience (Includes 1 and 5)
Being able to identify assets of greatest risks in your organization and having an active plan on recovery with intention of Recovery Time Objective and Recovery Point Objective in mind will go a long way.
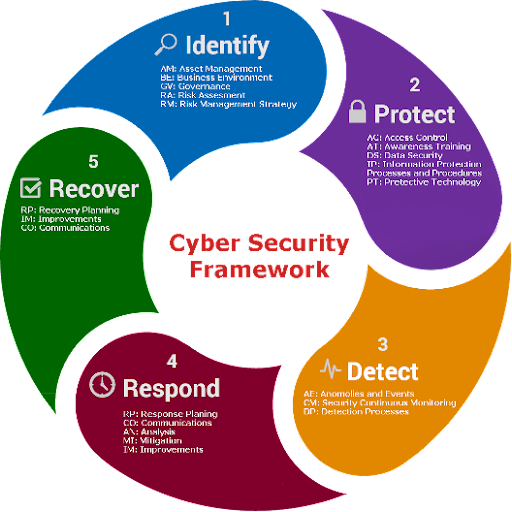
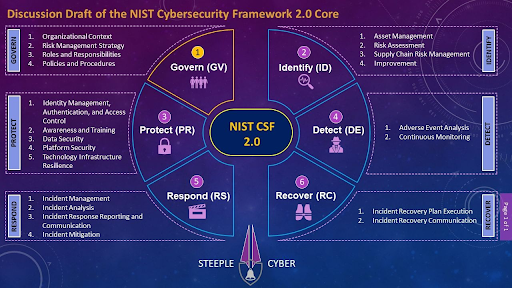
I however took a look at what Shaun van Niekerk, CISSP write up about The NIST Cybersecurity Framework 2.0 as illustrated below. I will advocate for you to read further in the link below
https://www.linkedin.com/feed/update/urn:li:activity:7056545104961892352/
Vulnerability Management:
Get to scan all systems and identify which are vulnerable or have outdated software and patch them with a plan (e.g Do not update Ruby packages blindly else you will have a long week). This is a low hanging fruit for many organizations yet they do not take advantage of it. Such practice can easily reduce your threat attack surface by a significant percentage. It will be a culture change but needs to be done regularly.
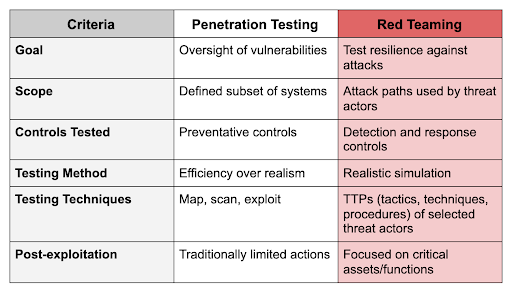
Penetration Testing vs Adversary Emulation:
It is nice to have Penetration testing done but that only goes for the low hanging fruits. Organizations need to start looking into performing Adversary Emulation with all sorts of Campaigns in place to close on all the loopholes from a RedTeam tactics point of view.
With that, you will be able to know the extent of an attack and/or if your Firewall/NAC/PAM/EDR/DNS Security tools etc are even working. Tweaking to optimization will be needed for many to reach some level of maturity.
Measure your Maturity level and stop buying new tools everyday:
Get to understand what level of maturity you stand with the various processes, metric, and tooling. This will range from Non-Existent, Initial, Repeatable, Defined, Managed or Optimized state. Not doing this makes organizations buy new tools without any focus.
A maturity check will guide in the future strategy of tackling operations, applications for security, endpoint security and infrastructure security.
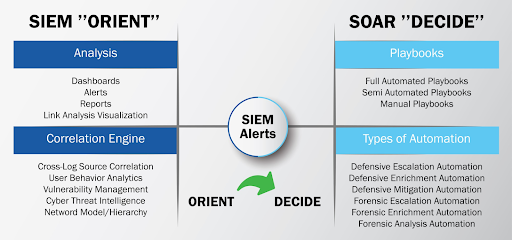
Threat Intelligence vs Threat Monitoring:
Most organizations get to have threat monitoring in place and that is because of compliance. The true usage of it is almost never realized thus incidence response becomes such a daunting task when they must sieve through thousands of alerts.
Threat intelligence is slightly different from just monitoring no matter how small or big your organizational assets are. Typical observation is not scoping properly of the toolset to put into the SOC, not fine-tuning what to be monitored and having engineers who are not properly trained with 2 people monitoring 1000s of alerts in a day. Not optimizing your security tools to collect the right logs for analysis and intelligence will let a lot of attacks slip through the cracks. A revamp is needed with effectiveness and efficiency defined for timely migration strategies to be recognized. With the above, an organization will be able to come up with the right usecases for threat hunting and also automate with a SOAR to reduce the amount of human intervention during an incidence. A SIEM will detect threats but a SOAR with the right playbook will be needed to remediate within the shortest possible time.
Cloud is not secure by Default (Devs vs Security):
The myth that “I have moved my assets to the cloud thus I am secure” is still lurking in the minds of many engineers. Cloud engineering needs a well-defined rollout plan for security with posture security always in place. As a lot of organizations are adopting public cloud infrastructure, there is a need to do a regular audit to make sure potential risks are closed.
Software Developers main aim is always focused on functionality and usability. Security comes as an afterthought and this feeds into the adoption of DevSecops in the everyday operation of organizations as they churn out new applications and move them to the cloud steadily.

Phishing attacks are not over:
The human element will always be an easy entry level for adversaries. Multi factor authentication has been a great help, but hackers have found ways to bypass them with a good phishing attack (I have tried in the past and succeeded enough times).
More than half of the organizations simple SPF and DMARC records are not set properly thus makes it easy to impersonate anyone in the organization (I have done this in less than 10 seconds).
API Security will be the end of your business:
There has been a significant increase in mobile and web applications over the years across the African continent. The interdependence on API integration with other service providers and urge to launch very fast leaves the majority of the APIs exposed to vulnerabilities.
Cyber criminals are exploiting these endpoints with ease to steal customer data and drain many wallets with ease and it is not about to end soon.
A simple adoption of OWASP Top 10 security measures(Web & Mobile) or implementing amazing tools such as WallArm security will go a long way. Wallarm also has many webinars as well as write ups explaining API Security that I believe everyone should take a look at in their spare time. This is going to be the biggest focus in the coming years and we are already experiencing them.
Insiders are still there:
Insider threats will be on the rise due to many factors, especially greed. In the African context, I have seen so many internal staff compromised to collude with threat actors from even the ransomware groups. A support engineer earning $300 a month gets to be targeted and offered $4000 a month just to allow for backdoors to be planted will easily accept that and has happened in the past.
Organizations need to adopt a Zero-Trust approach which is not a tool but a model. Please do not let vendors come to tell you they have a Zero-Trust too and you go ahead to buy. There is no one tool that does it all.
Extra view from Industry Experts
Discussing these issues got my good friend Sunday McDickson Samuel- SMS got him saying
“Remote browser isolation- building an airgap between the Internet and Internal networks, i.e., no codes of any will ever execute on the network, hence it’s impossible for drive-by-downloads/ exploits, browser vulnerabilities, watering hole attacks, phishing, malicious documents downloads, ransomware and ANY other Web or browser-based attacks getting. With RBI, detection and response-based tools will get a breather as NOTHING will ever trigger alerts to be detected or responded to.
AD and identity protection. The ultimate of any intrusion is to grab credentials, i.e., valid but stolen credentials. So, with an identity protection platform, you’ll be able to apply Risk-based MFA controls on ALL domain assets, i.e., workstations, laptops, servers, LDAP based applications including those legacy apps that were NOT designed to support MFA.”
Further conversations with Joseph Githaiga , an experienced data protection and privacy lawyer in a WhatsApp group gave some perspectives which needs to be taken in keenly when it comes to privacy and data protection.
Some key areas of focus in any organization when assessing exposure to data protection and privacy risk:
(1) Are the board and management aware of data protection laws and approved appropriate policies and procedures to comply?
(2) Does the organization have a designated data protection officer to monitor day to day compliance with the DP laws, guide employees in understanding their obligations, liaise with customers and the ODPC to address data protection queries?
(3) Has regular staff training been conducted to build awareness and create a privacy culture in the organization?
(4) Has the organization developed privacy enhancing documentation, e.g., a customer facing privacy notice that summarizes how the organization handles personal data in accordance with the law, a privacy policy that is internal facing to guide employees on how the organization handles personal data, a data retention policy that outlines how long the organization retains different types of personal data?
(5) How does the organization manage third party risk arising from outsourcing the handling of personal data to 3rd party service providers e.g., are there contracts in place obligating such 3rd parties to handle personal data in accordance with data protection laws?
(6) How robust are the organizations data security measures e.g., use of encryption, password protection, user access rights, data anonymization tools, SIEM tools, multifactor authentication?
(7) Has the organization put in place robust incident management measures that take into account the 72-hour breach regulator notification requirements under the law.
(8) is the organization aware of the rights that data subjects have under the law and has it put in place mechanisms to allow customers and other data subjects to exercise these rights?
(9) is the organization aware that all processing of personal data should be based on specific lawful grounds prescribed in the law and has it analyzed every processing activity to determine which lawful ground is applicable?
In summary, organizations need to:
- Go Back to Basics (Under Threats & Risks as well as How to tackle them)
- Use Business Model Disruption to Disrupt Security
- Position Cybersecurity as A Key Strategic Component of The Business (Boardroom conversations and if possible, appoint a Cyber Security personnel to join the Board)
- Translate technology needs to business benefits
- Prioritize People and Process
- Embrace Security by Design
- Adopt Existing Cybersecurity Frameworks and Standards
- Prioritize Continuous Monitoring and threat intelligence
- Understand Data Privacy and risks
- Move from compliance focus to risk based focus

